Not Beginner’s Stack (pwnable)
vulnerability
Let’s check the protection of the binary.
You can find that all protection is turned off.
1 | _start: |
They gave me source code. So it is easy to find where vulnerability is. Look at the vuln function. when read function is called, a vulnerability occurs. The buffer size is only 0x100. but the size that you can read is 0x1000. It is Buffer Overflow. Then i can overwrite the return address because the stack canary is turned off. and also i can use shellcode. (NX disabled). we can control the rsi by overwritting rbp-0x100. [lea rsi, [rbp-0x100]]. It means that i can arbitrary write.
So i changed retrun address to call exit into the address to call start for triggering bof again. I got many opportunities to trigger bof. I wrote shellcode on the section of 0x00600000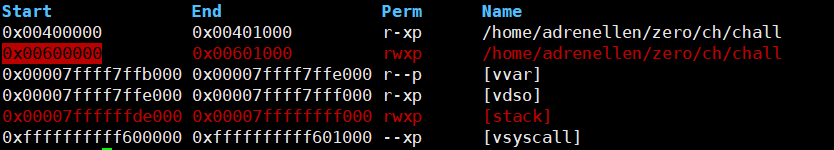
It was rwxp Permission, That’s why i used shellcode and wrote in there. Finally I overwrited return address to shellcode address and got the sh.
exploit
1 | from pwn import * |